Description
 |
 |

CLOUDASHUR ENCRYPTION MODULE KEY FEATURES
PIN authenticated, hardware encrypted,
cloud encryption module (patents pending)
Ultra-secure 7-15-digit PIN to authenticate the
cloudAshur module.
On-device Crypto-chip
Offering 100% real-time military-grade AES-XTS or
AES-ECB 256-bit Hardware Encryption with FIPS
PUB 197 certified USB 3.0 encryption controller.
Brute force hack defence mechanism
If the User PIN is entered incorrectly 10 consecutive times,
the User PIN will be deleted and the drive can only be
accessed by entering the Admin PIN to reset the User PIN. (Admin can change this from the default 10 incorrect PIN entries to 1-9, for the User only).
If the Admin PIN is entered incorrectly 10 consecutive times, all PINs and the encrypted encryption key will be lost forever.
Five-factor authentication
Something you have:
1. The cloudAshur hardware security module.
Something you know:
2. 7-15 digit Admin/User configurable PIN.
3. Username and password for the iStorage cloudAshur Windows or macOS client app.
4. Where the data is stored, and which cloud provider.
5. Username and password for the cloud account.
Compatible with Windows and macOS
cloudAshur client applications are compatible with Windows (7/8/10) and macOS (Sierra/High Sierra/Catalina).
Two encryption modes
The cloudAshur can be configured in two encryption modes AES-ECB 256-bit (FIPS Compliant) and AES-XTS 256-bit.
FIPS 140-2 Level 3 compliant tamper proof & evident design
All critical components within the cloudAshur enclosure are covered by a layer of super tough epoxy resin, which is virtually impossible to remove without causing permanent damage to the critical components.
If breached, the cloudAshur modules tamper evident design will provide visible evidence that tampering has occurred.
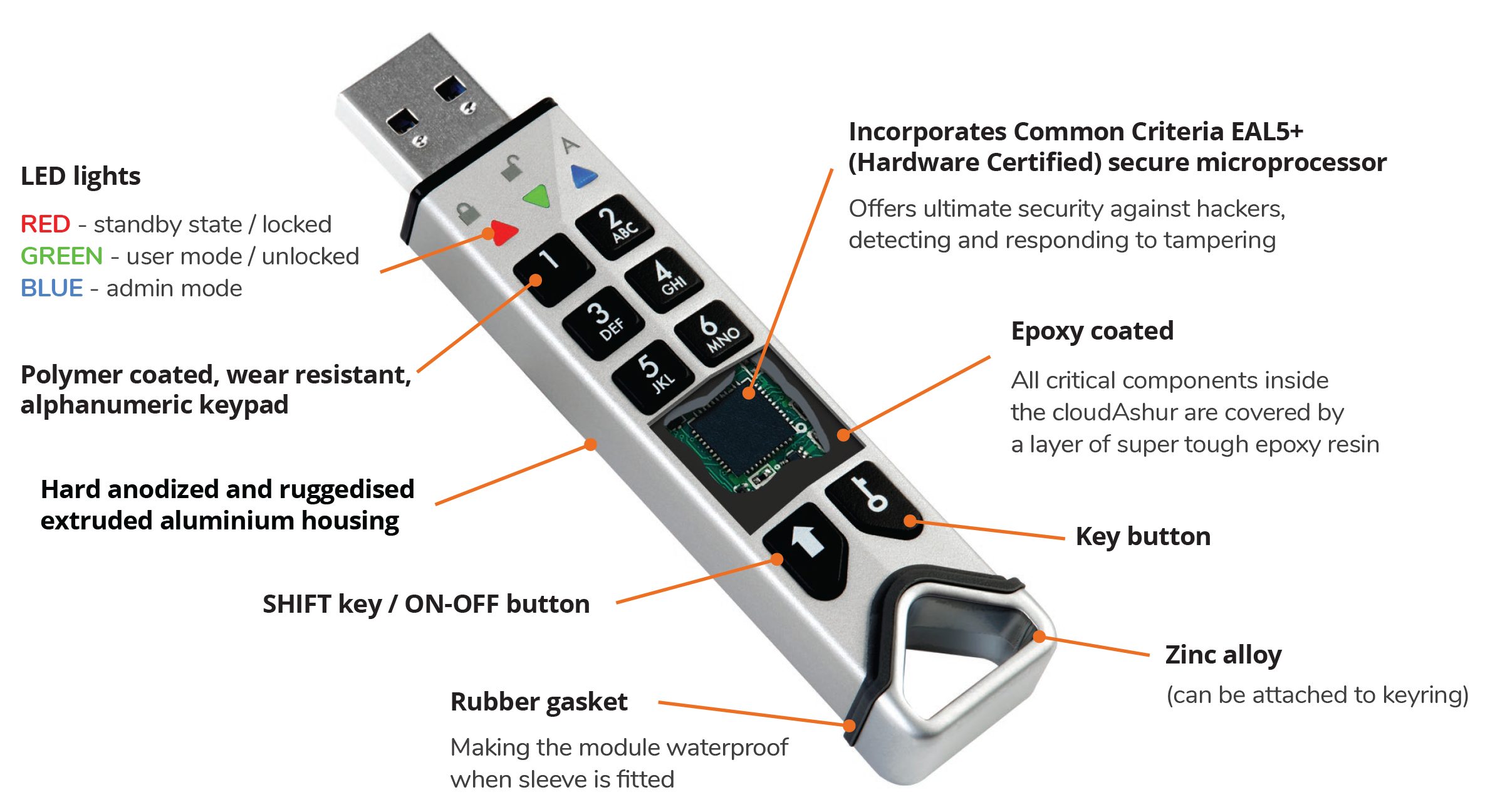
Incorporates a Common Criteria EAL5+ (Hardware Certified) secure microprocessor
Which offers ultimate security against hackers, detecting and responding to tampering with features such as:
- Dedicated hardware for protection against SPA/DPA/SEMA, DEMA attacks
- Advanced protection against physical attacks, including Active Shield, Enhance Protection Object, CStack checker, Slope Detector and Parity Errors
- Environmental Protection Systems protecting against voltage monitor, frequency monitor, temperature monitor and light protection
- Secure Memory Management/Access Protection
Polymer-coated, wear-resistant on-board alphanumeric keypad
The cloudAshur is authenticated (unlocked) and all functions are performed using the onboard keypad with zero host involvement. cloudAshur is not vulnerable to key-loggers and brute force attacks.
The cloudAshur keypad is coated with a layer of wear-resistant polymer for added protection.
Whitelisting on networks
Configured with a unique VID/PID and internal/external serial number with barcode, allowing easy integration into standard end-point management software (white-listing), to meet internal corporate requirements.
User PIN enrolment
The Admin can set a restriction policy for the user’s PIN. This includes setting the minimum length of the PIN, as well as requiring the input of one or more ‘Special Characters’ if needed.
The ‘Special Character’ functions as ‘SHIFT ( )+ digit’
)+ digit’
Inactivity Auto-lock
Configurable to lock after a predetermined period of inactivity. cloudAshur automatically locks when unplugged from the host computer or when there is no longer any power to the USB port.
Immune to Bad USB
Both the USB Cryptochip and Secure Microprocessor incorporate digitally-signed fl ash lock mechanisms making the cloudAshur immune to Bad USB.
Customisation services available
Offering an in-house PIN configuration and laser-etching service whereby the cloudAshur sleeve or side of the module can be customised with your name, company name and/or logo, web/email address, and phone number.
IP68 certified
Dust and water-resistant. Includes hard anodized and ruggedised extruded aluminium protective sleeve.
Separate Admin and User modes
Supports independent Admin and User PINs.
Self-destruct feature
Pre-program the cloudAshur with a self-destruct PIN, which once entered, the encrypted encryption key and all PINs are deleted.
One-time User recovery PIN
The Admin can program the cloudAshur with a one-time recovery PIN. This is extremely useful in situations where a User has forgotten the PIN to authenticate the cloudAshur.
This feature allows the User to enter the Recovery PIN and configure a new User PIN.